Introduction
A basic and quick approach to analyse phishing documents to identify indicators of maliciousness. FYI this post doesn't cover complete & in depth analysis of malicious documents
Tools
Run various rules against the sample document to identify any sort of maliciousness
The below rule can identify an executable file embedded in OLE objects
Run above yara rule against the downloaded document
Observe the below maldoc.yara output
It's interesting to see few suspicious Imports in embedded in binary
Again run other rules to get more confidence about maliciousness of the document
Now it's time for oletools and run oledump.py
A macro is observed in stream 8 and now run olevba to see the macro
Observe an executable name 1.exe
Run oleobj to see file embedded in OLE object
It's always interesting to see the metadata about any suspicious document and especially when the document is modified
Run oletimes to see the modification time of streams
Now it's time to dump the embedded exe file from document
Dump using -d option with stream number 14 in oledump.py
Open the dumped file in ghex an hexeditor and adjust the hex and ascii bytes to exe signature 4d5a at offset 0
Save as the file and run native file command and pecheck.py from Didier Stevens suite
pecheck.py can also parse the PE to preview it's imports
The extracted binary had been run on various sandboxes to identify any sort of maliciousness. Observe the below output from any.run
Report from Hybrid Analysis and researchers confirm that this malware variant belongs to hancitor downloader campaign. Below are indicators of compromise
Further analysis needs to be done to understand full functionality and characteristics of the specimen
A basic and quick approach to analyse phishing documents to identify indicators of maliciousness. FYI this post doesn't cover complete & in depth analysis of malicious documents
Tools
- Didier Stevens Suite
- sudo pip install oletools
- Yara - A pattern matching Swiss knife
Analysis
All document samples are pulled from Hybrid Analysis - a free malware analysis service for the community that detects and analyzes unknown threats using a unique Hybrid Analysis technology.
Hash 1: e07c84f98332b07ae40a22f15c32cbf794586e26576a7539def667881e15beae
Download above mentioned sample and check the integrity
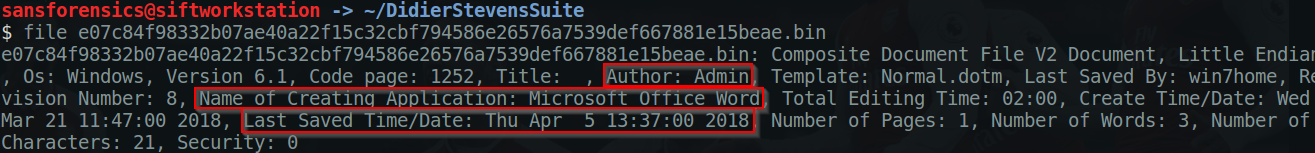
Check the file properties using native Linux file command which gives quick idea about sample
Download Didier Stevens Suite and check for yara rules.Download above mentioned sample and check the integrity
Check the file properties using native Linux file command which gives quick idea about sample
Run various rules against the sample document to identify any sort of maliciousness
The below rule can identify an executable file embedded in OLE objects
Run above yara rule against the downloaded document
Observe the below maldoc.yara output
It's interesting to see few suspicious Imports in embedded in binary
Again run other rules to get more confidence about maliciousness of the document
A macro is observed in stream 8 and now run olevba to see the macro
Observe an executable name 1.exe
Run oleobj to see file embedded in OLE object
It's always interesting to see the metadata about any suspicious document and especially when the document is modified
Run oletimes to see the modification time of streams
Now it's time to dump the embedded exe file from document
Dump using -d option with stream number 14 in oledump.py
Open the dumped file in ghex an hexeditor and adjust the hex and ascii bytes to exe signature 4d5a at offset 0
Save as the file and run native file command and pecheck.py from Didier Stevens suite
pecheck.py can also parse the PE to preview it's imports
The extracted binary had been run on various sandboxes to identify any sort of maliciousness. Observe the below output from any.run
Report from Hybrid Analysis and researchers confirm that this malware variant belongs to hancitor downloader campaign. Below are indicators of compromise
- wonyheghi,com
- tontwoverar,ru
- nofatiga,ru
Further analysis needs to be done to understand full functionality and characteristics of the specimen

















Great post. In step 10, oleobj extracted the Objects from the malicious file, although it's good to know that we can extract with oledump and adjust the file header.
ReplyDeleteHi thanks for sharingg this
ReplyDelete